The Recovery Time Gap: Why "Backups" Are Not "Disaster Recovery"
Most businesses believe that if their data is backed up, they are safe. They are wrong. The difference between "data preservation" and "operational restoration" is often measured in days of downtime.
In the immediate aftermath of a ransomware attack or server failure, the first question executives ask is, "Do we have backups?" When the IT director answers "Yes," a wave of relief sweeps the room.
That relief is premature. Having a copy of your data is not the same as having a functioning business. This is the Recovery Time Gap: the massive disparity between simply possessing your files (Backup) and being able to log in, run applications, and serve customers (Disaster Recovery).
For many organizations, this gap is discovered only during a crisis. They find that while their data is safe in a cloud vault, restoring it requires a functioning server, an operating system, and hours of configuration—infrastructure that may have just been encrypted or physically destroyed.
The Core Distinction
Backup is about files. It answers the question: "Can we get that spreadsheet back?"
Business Continuity (BCDR) is about time. It answers the question: "How quickly can we be operational again?"
Visualizing the Downtime: 52 Hours vs. 1 Hour
To understand the practical impact of this distinction, consider a standard scenario: a critical file server suffers a catastrophic motherboard failure or a ransomware encryption event. The chart below compares the recovery timeline of a traditional file-level backup versus a modern Image-Based Business Continuity (BCDR) solution.
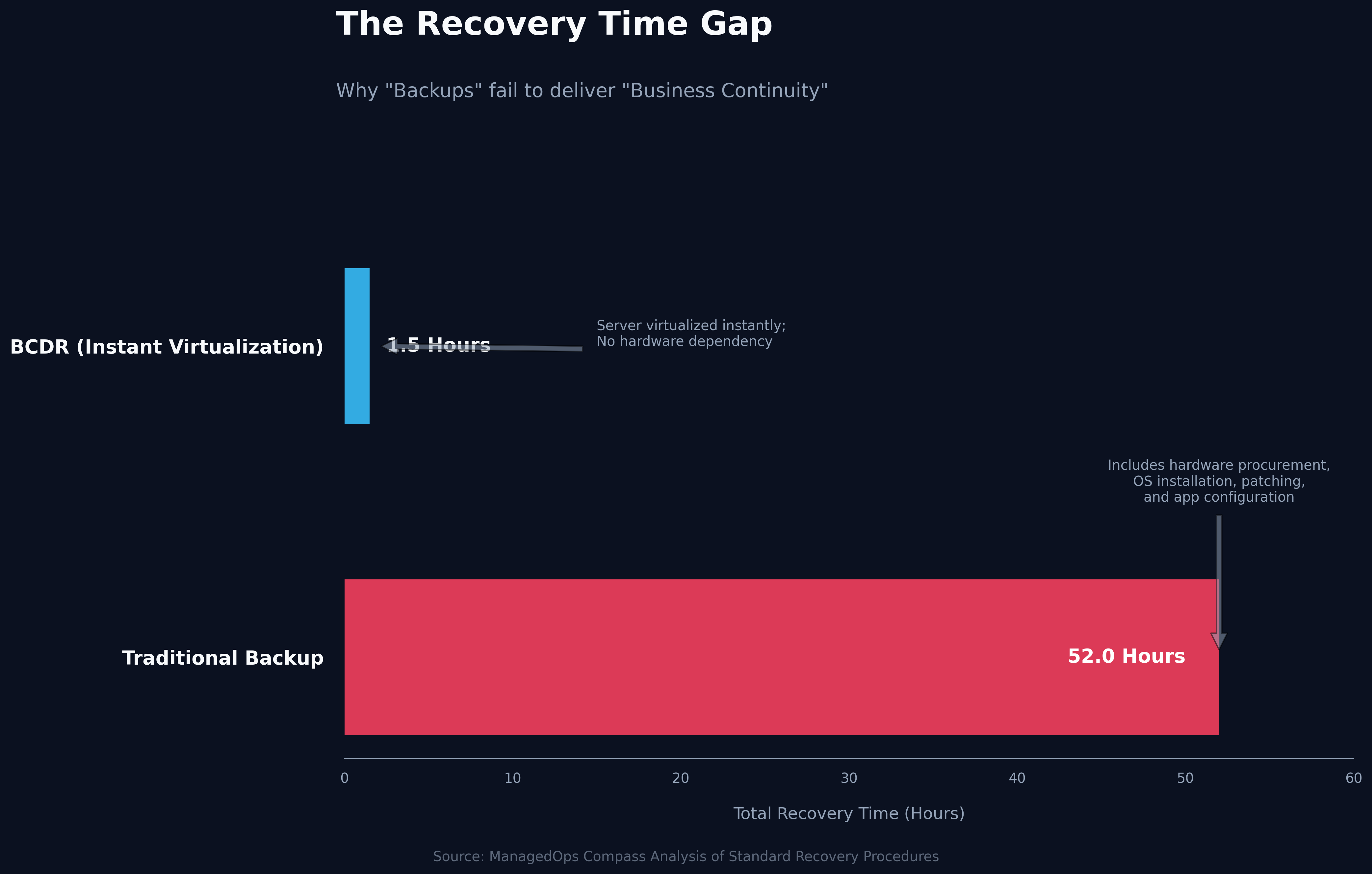
As the data illustrates, the actual restoration of data is often the last step in a long chain of dependencies. With traditional backup, you cannot restore data until you have a machine to put it on. This means diagnosing the hardware failure, ordering a new server (which can take days), installing Windows Server, patching it to the same level as the old one, and reinstalling applications. Only then does the data restore begin.
In contrast, Image-Based BCDR captures the entire "state" of the server—operating system, applications, configurations, and data—as a single bootable image. When the physical hardware fails, this image can be "spun up" as a virtual machine on a local appliance or in the cloud. The business is back online in minutes, while IT works on the physical repair in the background.
The "File-Level" Trap in MSP Contracts
Many Managed Service Provider (MSP) contracts include "Cloud Backup" as a standard line item. However, unless explicitly specified as "Image-Based" or "BCDR," this often refers to file-level backup.
File-level backup is inexpensive and excellent for recovering a deleted PowerPoint presentation. It is catastrophic for recovering a crashed Exchange server. If your contract does not specify Recovery Time Objectives (RTO)—the maximum allowable downtime—you likely have a file-level solution.
Why "Cloud-Only" Isn't Enough
Another common pitfall is relying solely on direct-to-cloud backups. While secure, downloading 4 terabytes of data over a standard business fiber connection can take days. A true BCDR solution typically includes a local appliance for instant virtualization, with a cloud copy for catastrophic site failures (like a fire or flood).
Three Questions to Ask Your Provider
To ensure you are on the right side of the Recovery Time Gap, ask your IT provider these specific questions during your next review:
1. "Do we have Image-Based or File-Level backup?"
If the answer is "File-Level," you are protected against deletion, not downtime.
2. "What is our contractually guaranteed RTO?"
If they cannot give you a number (e.g., "4 hours"), they are not confident in their ability to recover your systems quickly.
3. "When was our last Disaster Recovery test?"
A screenshot of a "Success" email is not a test. A true test involves spinning up the server image and logging into it to verify data integrity.
In the modern threat landscape, where ransomware is an inevitability rather than a possibility, the metric that matters is not "did we save the data," but "how fast did we get back to work." Don't wait for a crisis to find out which tool you bought.
This article is part of our series on Managed IT Service Models, helping you understand the technical realities behind service agreements.